Legal
Legal
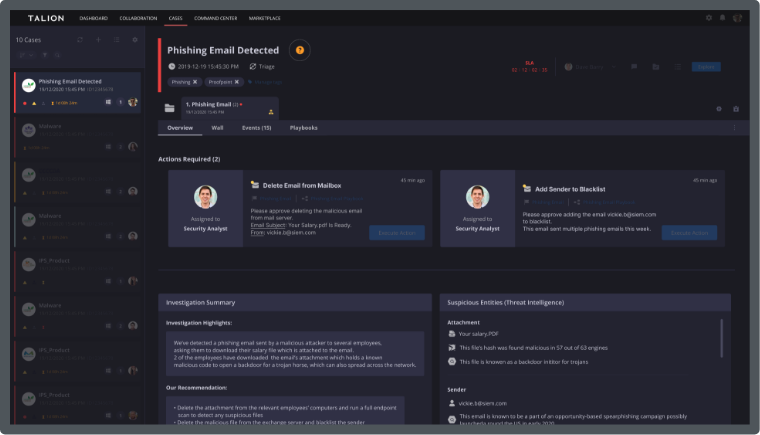
Law firms operate in constantly shifting environments where multiple client projects are on the go at any given time. In a fast-paced atmosphere, where communication is mostly conducted over email, it’s easy for hackers to infiltrate business documents and leverage the innate trust between attorney and client to access their network.
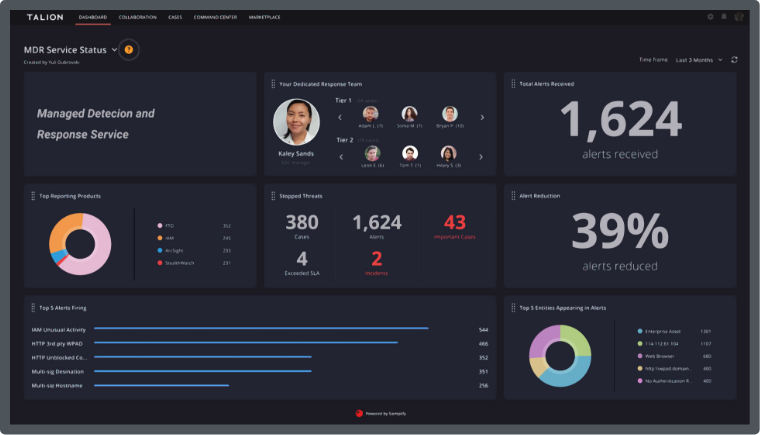
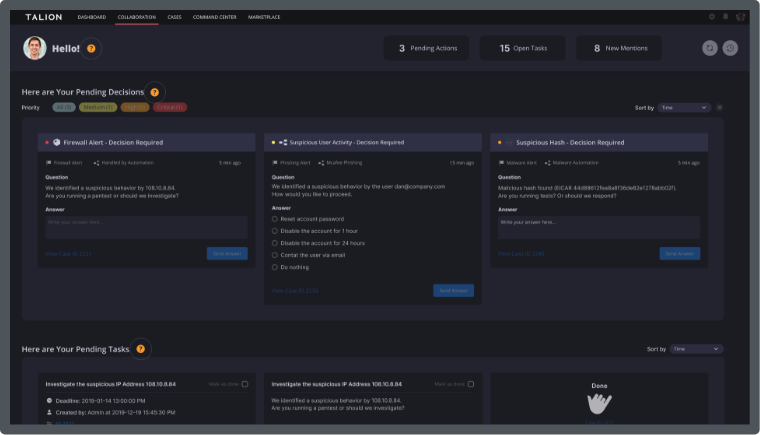
At Talion, we work with Law Firms to ensure sensitive and confidential client data is safe from cyber criminals, through bespoke Threat Intelligence and speedier detection & response capabilities, tailored to your needs.

According to ABA's 2021 Legal Technology Survey Report, 25% of law firms had experienced a data breach within the year.