Phishing remains the most common threat vector with 96% of phishing attacks coming via email. Last year, 36% of reported breaches involved phishing emails (up from 25% from the year before).
We live in a click society that is almost impossible to control. With advanced social engineering tactics and sophisticated tools that can bypass even the best software, including antivirus, it’s easier than ever to fall into the phishing trap. Your analysts are most likely drowning in email alerts from employees being phished, since attacks via email account for the highest percentage of threats.
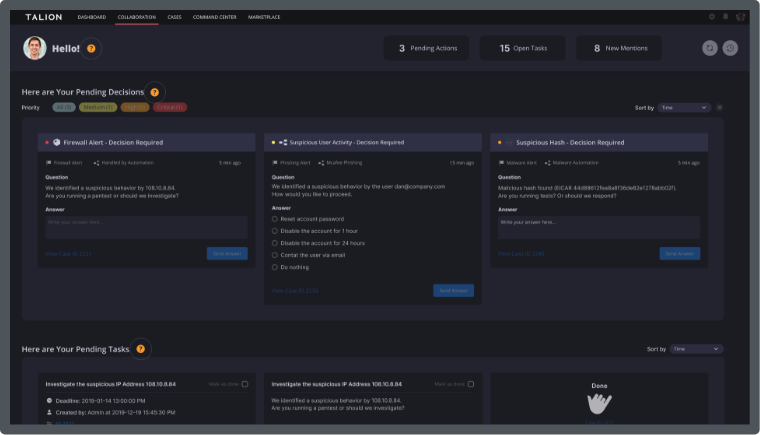
On top of that, your security team may be limited in numbers and don’t have the tools to determine positive/negative phish. Security teams also often lack the skills and 24/7 scope to address the most advanced phishing emails.
Read More
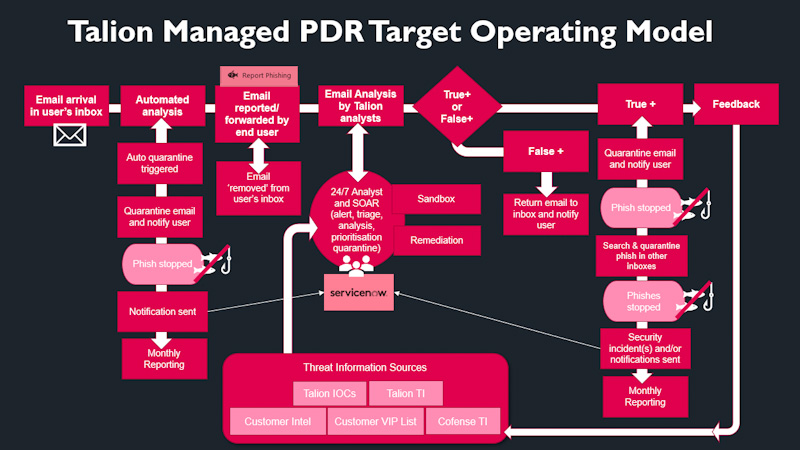
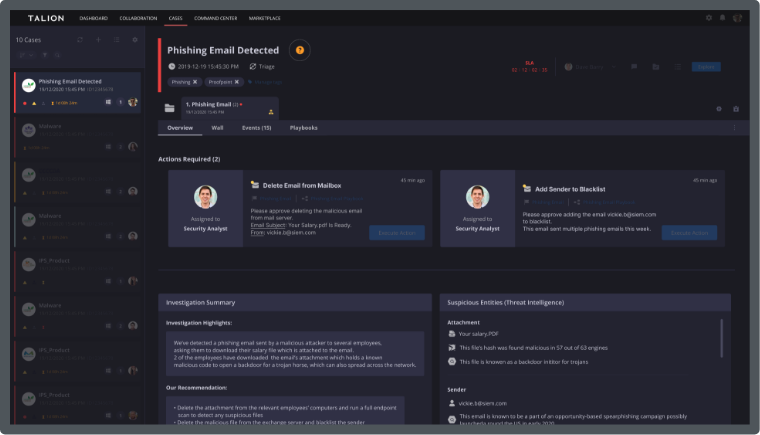
Managed Phishing Detection and Response solves these problems by blocking emails from known campaigns and provides a service that answers queries about phishes. It takes action to remediate positive phishes whilst informing the user and keeping your security team informed of the attacks against your user base.
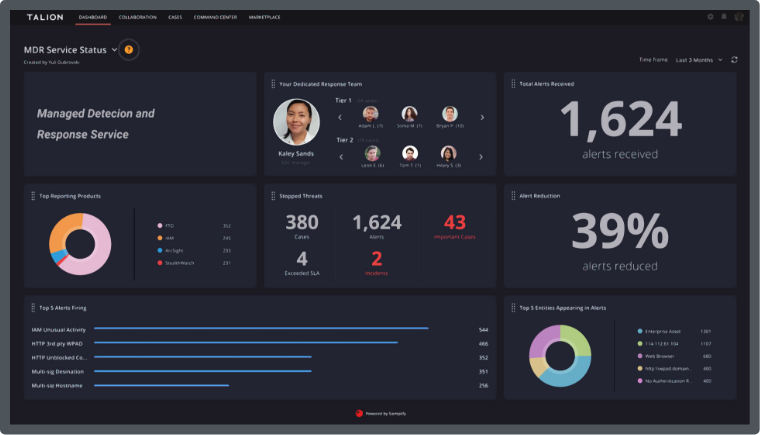
Talion’s Managed Phishing Detection and Response service works to quickly and effectively identify and stop phishing email attacks on a 24/7 basis.
Discover 5 tips to fight phishing and take action.
Read Less