Other Industries
Other Industries
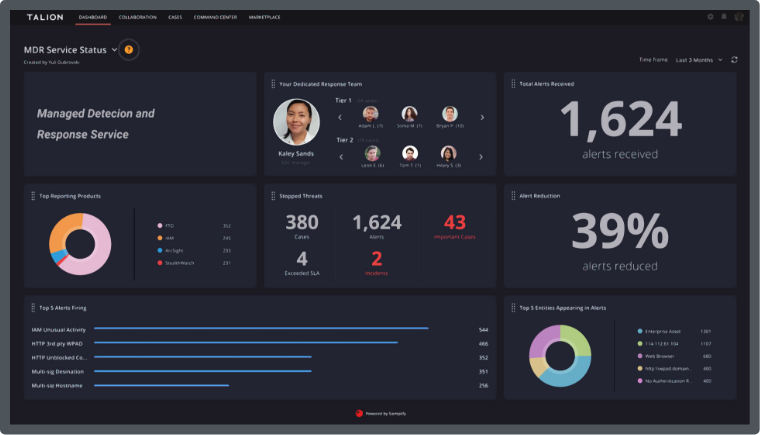
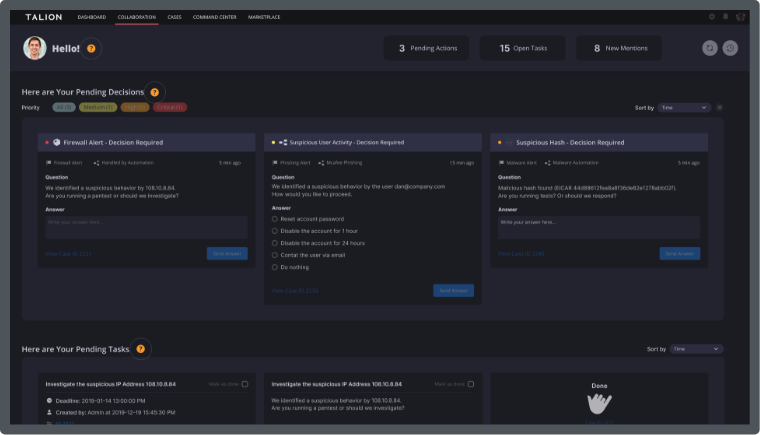
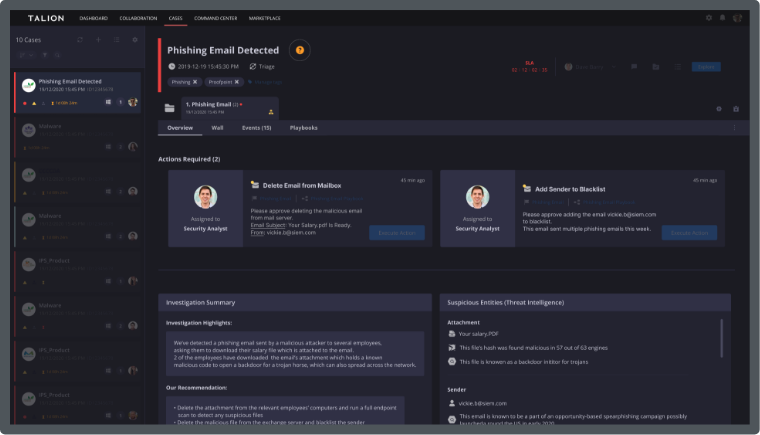
No matter what industry you work in, cyber security plays an important role. When cybercriminals trick employees with malicious links, networks go down and files are encrypted, it’s never easy to pick up the pieces, costing organisations not just time and money, but reputation and the mental health of staff working to remediate it.
At Talion, we work with numerous industries to ensure their network is secure and protected enough to keep business running smoothly. With our Hybrid approach, we help organisations find a security service that meets their requirement and budget, with as little or as much control as they like.

According to a global study of 1000 CIOs, 82% believe their software supply chains are vulnerable.