Manufacturing
Manufacturing
The Manufacturing industry is fast-paced in nature and uses a large number of technological equipment, but devices are often outdated and not designed to increase security, which makes them perfect targets for cyber attackers.
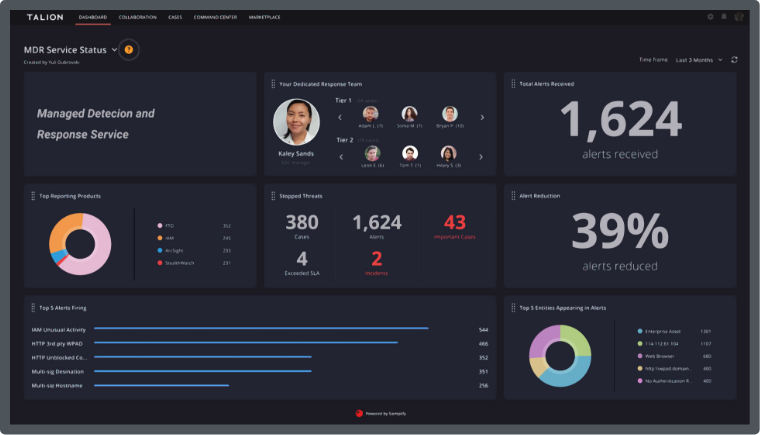
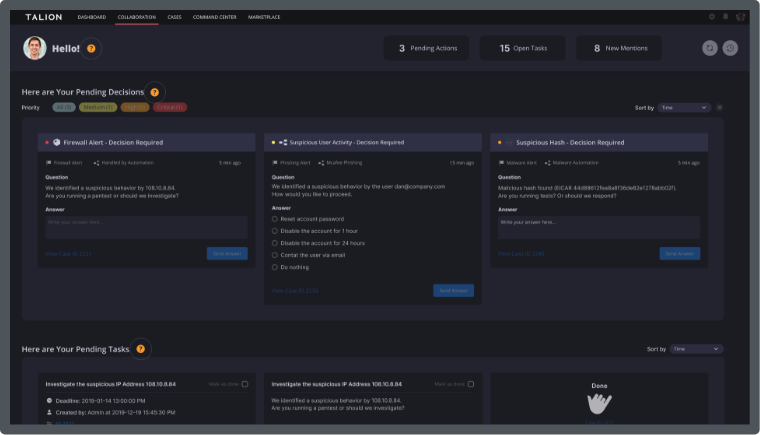
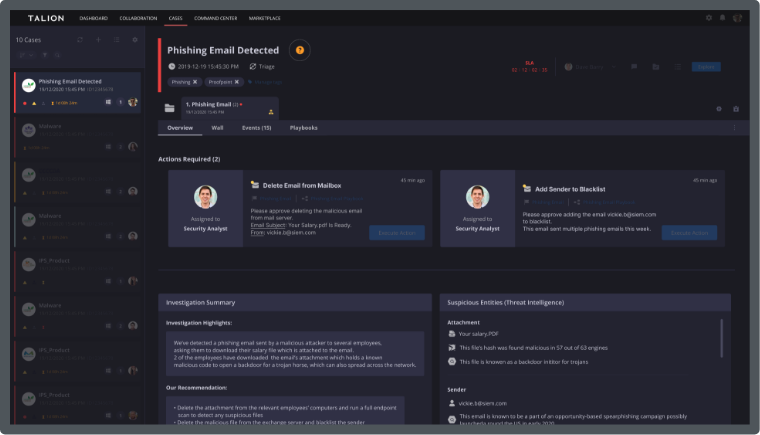
At Talion, we work with Manufacturers to help them assess their current security posture and face their potential threats head on. With our Managed Detection & Response (MDR) service, our team of analysts ensure sensitive information of supply chains and trade secrets is safe, so delivery and execution can continue without the risk of disruption.

According to an IBM report, Manufacturing companies account for nearly a quarter of all ransomware attacks - the highest targeted industry.