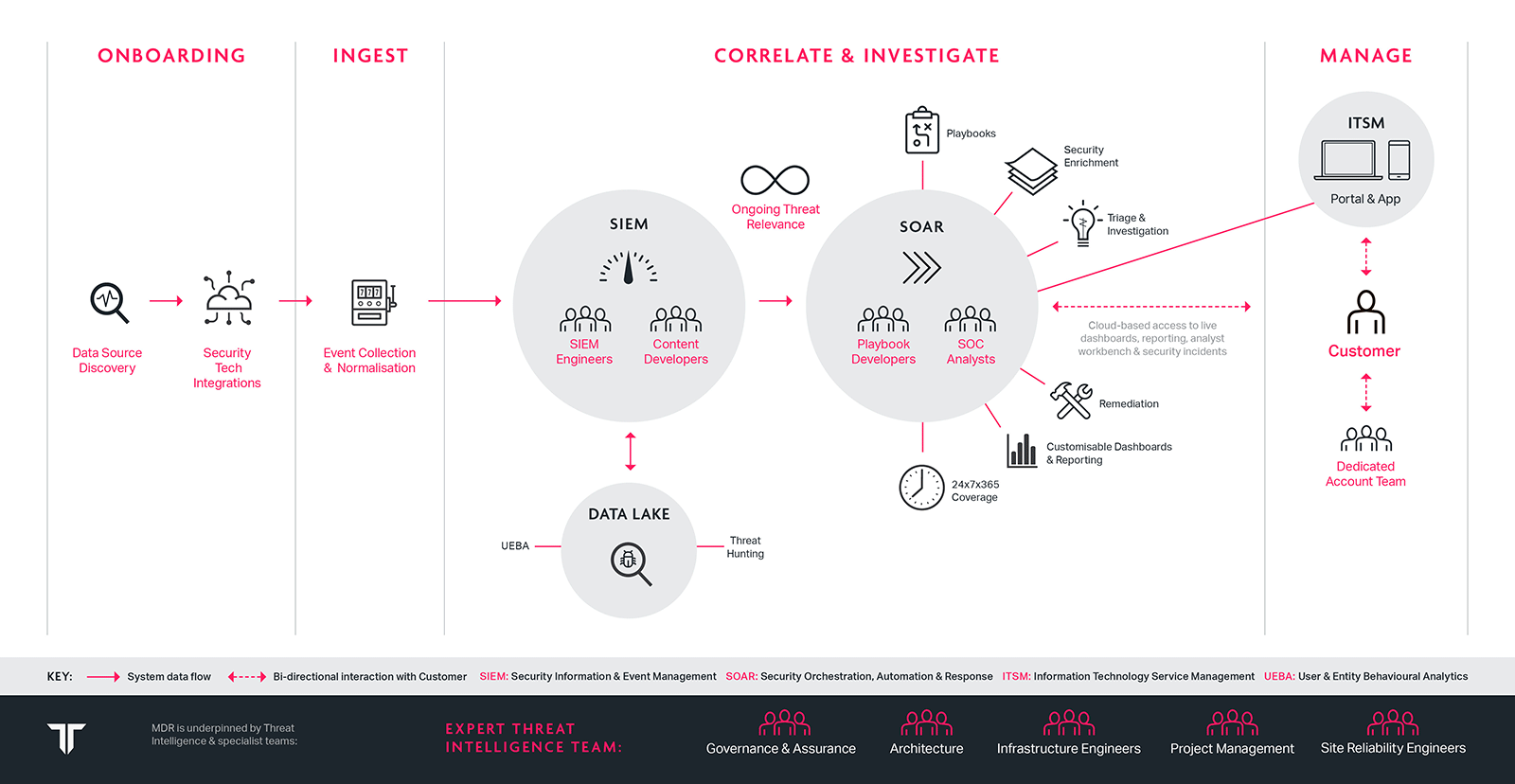
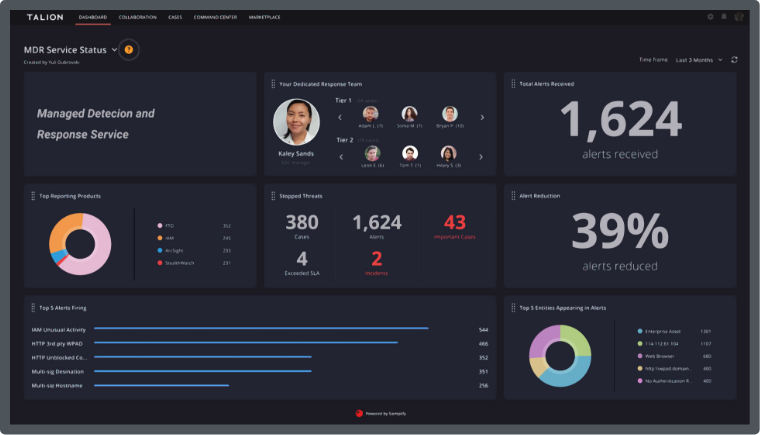
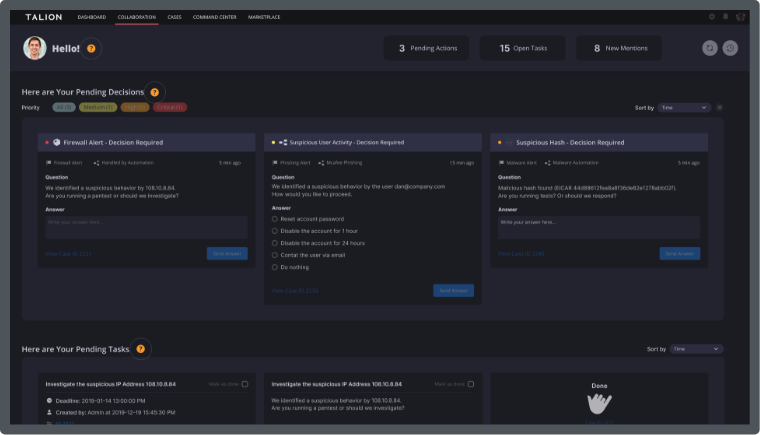
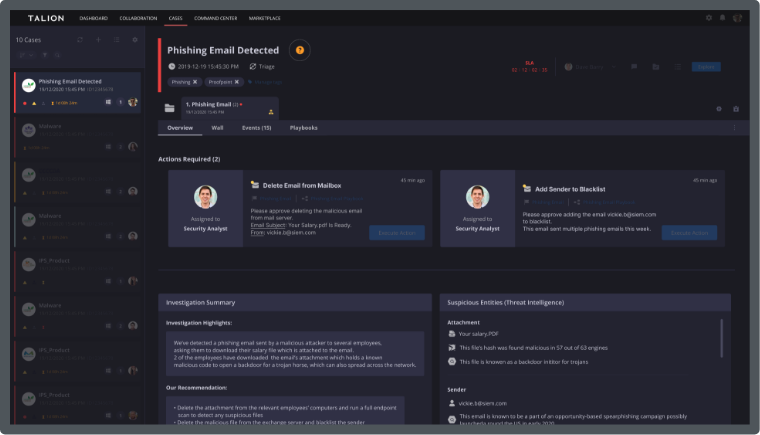
We also understand that you have already made investments in security solutions that you need to leverage and see value from. You need an always-on service, that detects threats, significantly reduces false positives, quickly, and where possible, automatically responds to attacks and provides human expertise through one-to-one collaboration to give context and guidance on how best to respond to threats.
Talion’s Managed Detection and Response service delivers all this and more. Our business started when the UK Government requested we protect a major global sporting event in 2012 – back then we were part of BAE Systems, the UK’s largest defence contractor. Today, we have the same defence grade platform, engineered to exacting standards, but we’re smaller, more innovative and agile, and easier to do business with.
Read Less